Friday, Feb 7, 2020

The magic of TOR
The internet is a vast, rapidly developing and constantly introducing invention into our lives. More than half of the world’s population is connected to this huge network. You can find devices connected to it everywhere. Figuring out who is where and who is doing what is possible in a matter of seconds. How’s that possible, you ask?
Intro
Internet is structured in a way that requires each interaction to be done one in a precise and systematic way. Single person, with high enough level of knowledge and a access permissions can easily figure out anything that has happen or is happening. So, shouldn’t that be reserved for catching the bad guys? Maybe, to a certain degree. The grid is full of malicious users, for instance spammers, attackers, malicious digital marketing firms and many more whose endgame is to use or violate our private data to their financial gain. Governments are also known to spy on people so they can fulfil their political agenda. Work of many activists and researchers has been exploited as a result of vulnerable infrastructure. Yet, even in today’s society, a good part of anonymity could be reclaimed with a few software tricks and some education.
TOR isn’t magic
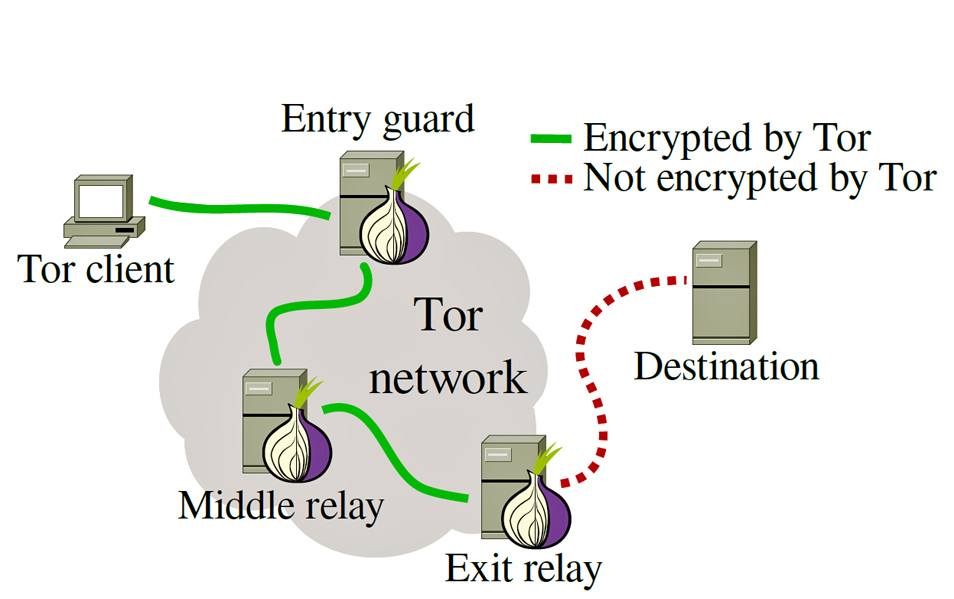
TOR (The Onion Network) is a group of volunteer-operated servers that allows people to improve their privacy and security on the internet, as defined on their official page. It creates a series of virtual tunnels between all nodes (also known as relays) of the TOR network. All of data transmission chooses a random relay (path) of tunnels. Onion routing technique is used with encryption and decryption mechanism to limit the knowledge of each node about that data that goes through them. They only know the relay path of which they are a part of, not the whole source to destination path.
I don’t need privacy, why should I care ?
People who keep saying that are often found to be the ones who have the most to hide. Let’s take an example: Person ends up having an embarrassing medical condition, he/she wants to find information about it without having Google and the rest of marketing companies knowing that. TOR is there to keep that information private. TOR browser isolates every visited website and prevents them from fingerprinting the user by making every user look the same. Cookies get automatically cleared so there’s no interest for the cookie monster in the marketing agency.

The magic circle
TOR anonymity is achieved by transmitting data though a TOR circuit, that is a key component of TOR which appends to onion routing mechanism. TOR circuit is basically a combination of entry, middle and the exit relay from the network. That’s why it’s named The Onion Routing protocol, because it adds layers at each stage. Part of transmissions also engage Bridge nodes. Bridge nodes are used in scenario where publicly known entry and exit nodes are being blocked by a certain party.
“Onions have layers” - Shrek
The wonderful wizard of Oz demystifies entry nodes
To put it in simple terms, guard relay is an entry point to the TOR circuit. Every client that connects to the network will first have to connect to a guard node. That means the guard node has access to the real IP address of the connecting user. List of guard nodes is publicly available and it’s constantly updated on the TOR metrics page (mentioned later). There were some cases where hackers would take control over certain relays seeking to get access to browsing sessions. Users may notice when they try changing the circuit in their current session, it changes all the relays except the entry node. Why does that happen? It is explained below, under guard pinning.
What about middle relays ?
Middle relays secure most of the TOR circuits in any transmission. They are made of nodes through which data is transferred in an encrypted format. None of the nodes have access to the packet information, same as their predecessors and descendants. All of the middle relays are accessible to entry and exit nodes so that those nodes can pick ones that are available for the transmission. In a scenario where middle relay has been acting maliciously, policy does not allow it to reroute traffic. Middle relays can’t act as exit nodes, and they’re most suitable for hosting TOR from home or work.
Magic realm of abuse complaints
Exit nodes are the final relays in TOR circuit. Their purpose is to send the routed traffic to a set destination. They’re often considered ‘criminal’/’illegal’ because those nodes are perceived as origins of all the traffic that exists them. So, the exit node’s IP is visible to the destination, and they often receive complaints, legal notices, take down notices. TOR user base is diverse, so you can’t expect everyone to act by the rules. If someone is to host an exit node, they need to make sure their ISP is okay with it, and be ready to deal with notices and all kind of legal mayhem.

Yellow brick road
Huge part of entry and exit nodes get blocked by parties that want to restrict the access to TOR network. Large number of corporations, ISPs and governments have filters to ban TOR network (China, I’m looking at you). That’s why bridge nodes are not publicly listed. Obfuscated bridge nodes turn out very useful for places where using TOR is considered suspicious or even dangerous. They act as relative entry points to the network, making it hard for the ISP to notice traffic to the TOR network.

Guard node pinning
During the first start-up of TOR client, it picks a small and random set of guard nodes. In the course of next few months, it assures that those pre-selected entry nodes are being used in the circuit. Guard node pinning is really important because of TORs threat model. For the reason that single vulnerable circuit can destroy data integrity, TOR tends to minimize the probability that it will ever create one or more of the vulnerable circuits. In the event of an attacker resolving the guard nodes and trying to shut them down, TOR has algorithm in place which will detect this and reroute the connection.
Got to save them all
The state of TOR network is constantly tracked and publicised by a group of trusted servers which are known as directory nodes. Every individual node is controlled by a different organisation. Those organisations offer redundancy and are able to distribute trust. Integrity of the network itself relies on the correctness and honesty of those directory nodes. Directory nodes maintain a list of running relays which are then publicly listed. Every hour those nodes publish a consensus which they verify together, and it ensures that all clients have identical and correct information of available relays. Relays send a notification to directory nodes each time they’re online.
The infinite question

TOR versus VPN! During a usage of VPN, it forwards all of the traffic to specified destination. All along that process, all of the traffic gets encrypted by VPNs certificate. That means the ISP can see the encrypted traffic is flowing to the VPN server, but they can’t see inside it’s contents. Problem with VPNs is that it doesn’t protect the user from itself, that server is basically a man in the middle. It knows who you are, who you are talking to and how to decrypt traffic data. That’s the main issue with VPN, it requires heavy TRUST. I don’t know about you, but trust requires a lot of sacrifice, and I’m not willing to take that gamble. In TOR, one rogue node is endurable. If one of the nodes is rogue, it’ll only know the entry IP OR the data packet. Which means TOR protects the user from itself. So, compared to VPN, TOR does not require as much TRUST.
TOR
| Pros | Cons |
|---|---|
| User friendly | Can be very slow |
| Platform is free | Could lead to legal trouble if misused |
| Safeguards privacy + encryption | Some web services are blocked |
VPN
| Pros | Cons |
|---|---|
| High speed | Software failure |
| Full access to services | Expensive unless self deployed |
| All system traffic is encrypted | Providers monitor activity |
Selling illegal things
Whenever people talk about ‘deep-web’ or ‘dark-web’ they’re actually talking about TOR hidden services. The whole concept is really wild and complicated. Hidden service is a classic web server that listens only on TOR network. How does it work ? The device can access the service, but it has no information about the server, nor the server has any information about the client. Server has 3 relays which are acting as ‘introduction points’. Hidden services are not indexed when created, only the person which has the key (.onion) address can actually access it. Because of that, index pages have been developed, where websites can be submitted for people to find them.
How do I use it ?
Easiest way would be to download TOR Browser. It is based on Mozilla Firefox, with preset security settings and plugins. This has been made so users would not have to manually setup network settings and plugins, or should we say to avoid a security catastrophe. What if my Windows is leaking ? Tails is a portable Linux distro which has been developed with intention not to leave a single trace on the system. It runs as a live USB, purely in memory and leaves no trace on the drives. During shutdown, all of the memory gets overwritten. In case a user needs storage to save data, persistence feature has also been added. All the connections from Tails are routed through TOR network, and it comes with pre-installed secure software for chat, browsing, storage, metadata removal etc.
I want to help!

To keep this short, official guide is located here. You’re going to need a VPS (virtual server) or your own unused PC in case you’d like to use your private bandwidth. The environment I would personally recommend would be to run TOR service on a minimal Linux based system. Make sure to set network limits in case of limited bandwidth or connection sharing with other machines on the network.
How can I do more ?
- grow the Tor network,
- demystify relay operation for newcomers,
- organize important relay resources in one place,
- encourage everyone who reads it to support the Tor network by setting up their own relay,
- make the Tor network more robust (example: To reduce the overall fraction of outdated relays, we added instructions for enabling automatic updates),
- emphasize diversity on network and OS level (Most of the Tor network runs on Linux, so we emphasize OS-level diversity and encourage people who can to run BSD-based OSes).
Terms of services
Most of server providers do NOT allow TOR in their terms of use agreement. This is a list of a few providers I’ve had good experience with: * VpsBG – allows crypto payments, okay with relays, bridges and exits. * Contabo – allows all nodes, you have to deal with complaints. * FlokiNET – allows all nodes, sponsors saveyourprivacy nodes. * KoDDoS – allows all nodes, supports crypto payments. * HostHatch – all nodes expect exit, direct transit to 4 datacenters. * Psychz – allows all nodes, very exit friendly.